In this follow up to part one, I introduce a couple of different canvases (see e.g. Lean Canvas), that can help you to start developing your information security in a human-centered way. The first canvas is suitable for the initial mapping of a project and defining its objective and current status. The second canvas aims to bring attention to the individual in the middle of all the ISM development. What’s the weakest link like this time and how could it be strengthened?
The development process of human-centered information security management
All projects must start with definitions. What is the objective or effect we’re aiming for? How is it measured? What’s the framework we’re working in, how do we frame the project? What do we know about the subject already, and what do we need more information on? The list goes on.
After the definitions, the project can proceed by following the steps below, for example. Later – with some relevant adjustments – it can even be used to create a continuous development process that takes place alongside normal business.
- The first step is to find that (in)famous ‘someone’, i.e. the operative owner for the development work, and get them up-to-date on their task. In my opinion, this task cannot be outsourced outside the organization. If the aim is to develop the organization’s safety culture, the control cannot be given away. However, this doesn’t exclude getting some relevant expertise and help from the outside if need be.
- Make plans concerning the way things are going to be carried out and the people you need to involve and think about how you can engage people on their own terms. Create a backlog.
- Broaden your understanding of the current situation by interviewing selected individuals and try to understand the context of the development work, needs of the people, development targets, challenges, etc.
- Discuss the results of the interviews, identify targets for development and add work to the backlog.
- Bring people together and identify the asset in need of protection as well as the risks involved. Assess the risks by using the organization’s risk management model. If there’s no model, adopt one, basing it on, for example the ISO27005 standard
- Continue by discussing the risks together. Plan and decide the methods used to manage the risks. Add work to the backlog.
- Implement management methods in the agreed order of priority. The order can be affected by things such as risk level (low-high), the time/money/other investment required for implementing the method (bear in mind it’s not worthwhile to make the investment larger than the damage caused by the potential realization of the risk), ease of implementation and people’s approval, dependencies with other tasks, etc.
- Implement solution/management methods by collecting more information on people’s needs, involving them in the solution design process, and testing the solution with the people‘s help. Carry out iterations based on the feedback.
- Regularly assess the functionality and effect of the development process and management methods, for instance, in retrospectives. Add work to the backlog.
- Repeat from step 5. Over and over again.
Clarifying the initial set-up
Good questions are a designer’s most important tool (along with the ability to challenge prevailing conditions). However, asking questions about the initial set-up during different types of discussions with different people at different levels of the organization soon creates a need for memory aids and ways of arranging and distributing information. Whether the discussions are held privately or in a bigger group (in a workshop, for example), canvases can provide a great help for the needs mentioned. In essence, they’re like a floor plan, showing you where you are and where you should go next.
The following canvas may help with the initial mapping of a project. It can be used as an interview structure to facilitate discussions, or it can be filled out during a workshop group exercise. The biggest benefit will be gained if the canvas is afterwards put on display in a place like the office wall or the homepage of a digital workspace where many people can see it and where it can inspire further thoughts and actions.
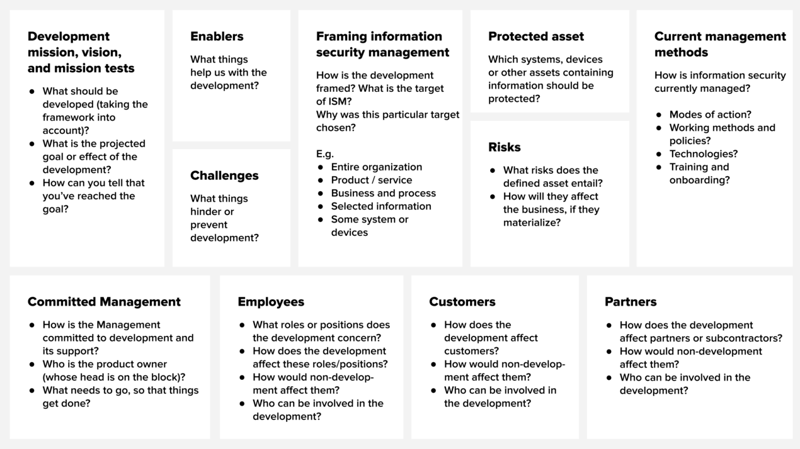
What’s the weakest link like?
All designers and product developers know that coming up with a useful solution that the user needs and that becomes part of their everyday life is challenging. It’s particularly difficult if we don’t know the end user and have no idea about their needs or the context in which the solution is going to be used. Here’s where good questions will come in handy again. They will enable us to collect information about the users’ work and its security aspects. Empathy mapping can offer a great tool that can be used to support interviews and distribute subsequent insights.
Based on the idea of empathy mapping, I outlined another canvas that aims at paying attention to the role of an individual caught in the middle of information security management. Ask yourself this: What is the weakest link like this time? How could it be strengthened?
Use the canvas as an interview support. You can collect the information on one role or position onto the canvas, for example, and discuss the findings together in a workshop. It’s a good idea to return to this empathy mapping again and again, as you learn more about the people and when you need to remind yourselves of the individuals whose work your management method or information security solution is going to affect.
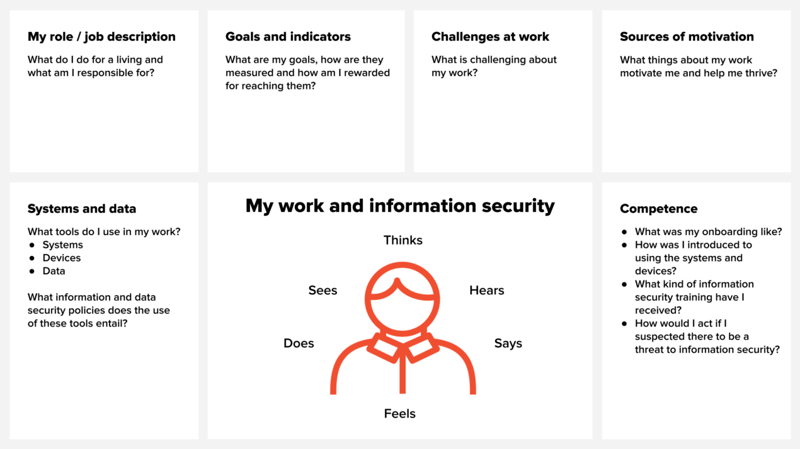 Individual at the center of information security management.
Individual at the center of information security management.
Some final words
Sadly, I haven’t yet managed to test the canvases in practice. If you happen to try them out, I’d be grateful if you shared your experiences and sent me some feedback. Did they help you with your thinking, interactions and joint development?
If you’re someone working in digital services, I hope these thoughts have given you some food for thought. If you want to delve deeper into human-centered ISM, here are some thought-provoking works that I would recommend:
- Thinking The Human Factor: A Philosophical Approach to Information Security Awareness Behaviour and Culture
- The Psychology of Information Security



